Server Architecture
- Home
- Neuron ESB
- Architecture
- Server Architecture
The container for the Neuron ESB server runtime is a single Windows Service Application named the ESB Service. The ESB Service reads its configuration and creates a collection of child services, each in its own AppDomain. As shown below, the child services provide connection, publishing, messaging, and infrastructure services.
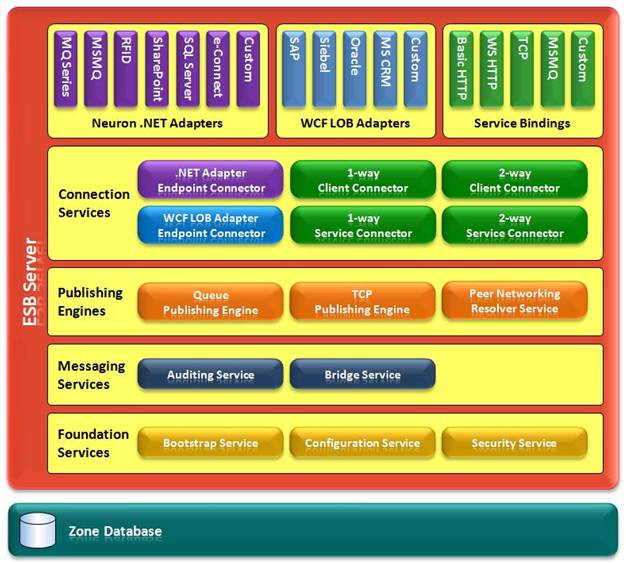
Adapters and Bindings
The adapters and bindings provide connection to service-oriented endpoints and non-service endpoints. [suggestion delete this sentence ] All three represent extensibility points to connecting new kinds of systems and services to the ESB.
WCF Service Bindings provide connections to web services.
.NET adapters provide easy-to-write .NET connections to systems and resources.
WCF LOB adapters provide connections to legacy systems and line-of-business systems.
Connection Services
Client connectors allow applications to connect to the ESB using web services.
Service connectors allow the ESB to connect to web services. When combined with a client connector, service connectors can provide routing and mediation.
Adapter endpoints maintain a connection to additional resources and applications. Based on the capabilities and configuration of the adapter, the adapter may be a message source or a message destination.
Publishing Engines
Publishing engines provide server-side support for various types of topic channels. Peer, TCP, and MSMQ topics require a publishing service to facilitate communication.
Messaging Services
An Auditing Service stores sent and received messages to an audit database for topics that have auditing enabled in the configuration.
A Bridge Service provides real-time or queued-relay bridges across topics and zones
Foundation Services
The Bootstrap Service provides a connection point to the messaging fabric for endpoint applications.
The Configuration Service provides publishers and subscribers with configuration information.
The Security Bridge Service provides authentication and authorization of parties.