Identity Propagation
- Home
- Neuron ESB
- Development
- Samples and Walkthroughs
- How To
- Identity Propagation
This How To will describe how you can enable Identity Propagation with Neuron for Service Endpoints. Utilizing this feature enables requests from clients to flow identity as they pass through Neuron ESB Client Connectors and Service Connectors.
Neuron’s identity propagation for Service Endpoints relies on Kerberos. Kerberos is a large and complex topic and this How To is not about configuring Kerberos. It is assumed Kerberos is active and functional in your Domain.
Identity propagation necessarily involves elevated permissions.
Concepts
Kerberos has 2 different types of accounts. One is a User Principal Name. The other is a Service Principal Name. Both accounts must be unique across your entire AD forest. Service Principal Name’s are automatically created for Computers. If Neuron is running as Local System it will use that computer’s SPN unless it has been removed.
For Kerberos to function effectively you must have DNS and NetBIOS configured correctly in the Domain and you must have all machines time synched to be within 5 minute of each other.
Finally, the extent of configuration needed is dependent on your topology. Domain security policies can make configuration more complex or completely disable the ability for Delegation to function. That being said, the following guidance has been tested:
- If the service you are connecting to as an impersonated user is on the same machine as Neuron and you are running Neuron as Local System then you will likely be able to simply check a few boxes, use unconstrained delegation, and select from a drop down and everything will be taken care of for you.
- If the service you are connecting to as an impersonated user is on a separate box then you are going to need to
- Create a Domain user account to run the Neuron ESB service (Do not add that account to the Domain Administrator’s group)
- Use SetSPN to register the neuron account for the necessary protocols on the server (This may require adding a DNS CNAME if Neuron is sharing the server with other services running as the computer account)
- Add the service account to the Local Administrators group on the Neuron server
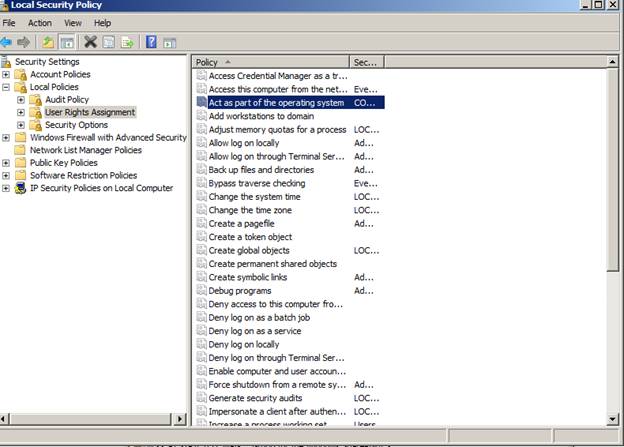
- Using the Local Security Policy tool add the User Right Assignment Act as part of the operating system
Step 1 Kerberos Delegation
Configure Neuron server for delegation. This is done with the Active Directory Users and Computers tool.
The picture blow shows Constrained Delegation
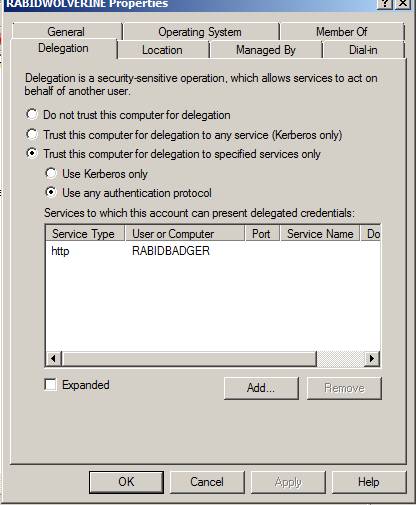
Unconstrained delegation is when you choose the second option Trust this computer for delegation to any service. Unconstrained delegation should not be attempted if the service Neuron is connecting to is on a different server.
If you are configuring Neuron to run as a custom service account you must also configure delegation for that service account.
If you do not see the Delegation tab then you likely have not set an SPN for the service account using the SetSPN tool ( SetSPN {Service Name}/{Neuron Server Name}:[optional port] {Neuron Service Account}).
It is sometimes necessary to add unconstrained delegation to the account, save the record and then reopen the record and change the delegation to constrained.
Step 2 Configure Service Rights
If the Neuron service only needs to connect to services running locally as the impersonated user and is running as Local System you are finished with operating system configuration
If you are connecting to a remote service from Neuron and using a custom service account you must add the service account to the Local Administrators group and you must use the Local Security Policy tool to add the Act as operating system right.
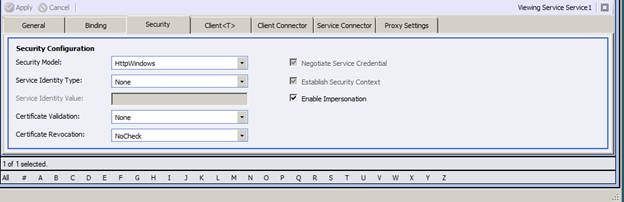
Step 3 Configure Security for the Service and Client Connector
The Service and Client Connector tabs must be configured with security options that allow for impersonation. This is controlled in the security tab. The setting below shows the setting for Integrated Windows Authentication using the BasicHttp option
Considerations and Caveats
Impersonation and Kerberos are complex to manage and require that DNS and NETBIOS resolution are functioning perfectly and that SetSPN has been used perfectly.
In addition many companies have policies against settings required for proper functioning.
Neuron does not control the vast majority of factors required to make these scenarios work.